zkVM Overview
WARNING: This software is still experimental, we do not recommend it for production use.
If you're ready to start building, check out our zkVM Quick Start and our zkVM example applications.
The RISC Zero zero-knowledge virtual machine (zkVM) lets you prove correct execution of arbitrary Rust code. By allowing users to build zero-knowledge applications that leverage existing Rust packages, the RISC Zero zkVM makes it quick and easy to build powerful verifiable software applications. Our demos show how to:
- use chess crates to prove mate-in-one
- use JSON crate to make proofs about private data
- use JPG crates to prove you can find Waldo
- use Rust-Ethereum crates like revm, ethers, and alloy to prove correct construction of Ethereum blocks.
On any other proving platform, building any of these projects requires starting from the ground up. By letting developers use the primitives they need, the RISC Zero zkVM makes verifiable software development a practical reality for projects of all scales.
We're focused on delivering a first-class developer experience together with first-class performance. We offer an open-source prover that can prove computations of any size on standard consumer hardware, and we make it easy to request/receive proofs remotely with Bonsai.
The documentation on this site will teach you how to write software for the RISC Zero zkVM, how to use the zkVM to generate proofs on your own machine, and how to use Bonsai for remote proof generation.
zkvM Quick Start
Building a zkVM Application
The core of a zkVM application is the guest program. The guest program is the part of the application that gets proven.
To prove correct execution of the guest program:
- The guest program is compiled to an ELF binary.
- The executor runs the ELF binary and records the session.
- The prover checks and proves the validity of the session, outputting a receipt.
Note: You only need to worry about the details of step 2 & step 3 if you're running the zkVM on your own hardware. See Host Code 101 for more details on these steps. If you're using Bonsai for remote proving, you won't need to write host code.
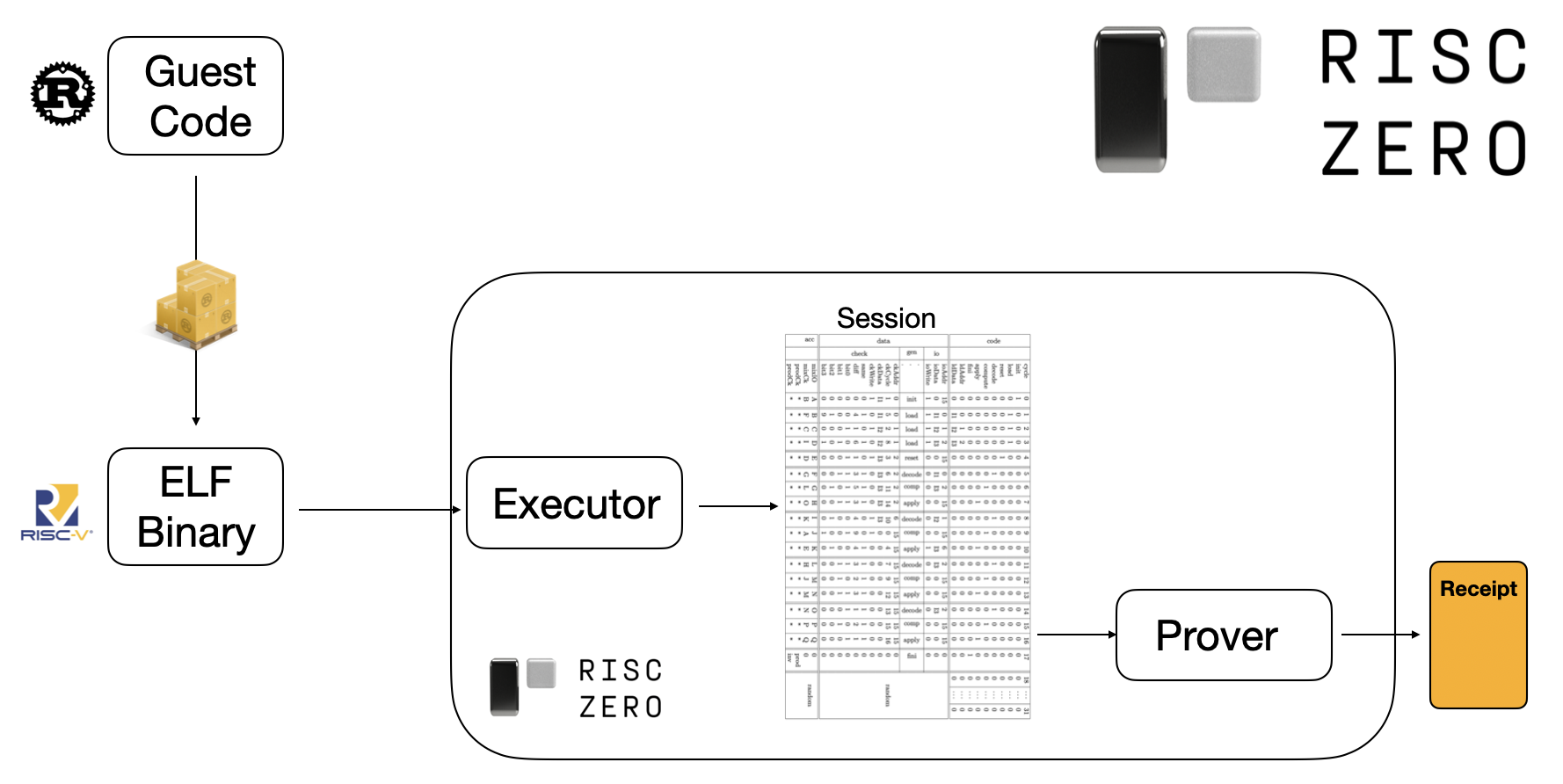
Anyone with a copy of the receipt can verify the guest program's execution and read its publicly shared outputs. The verification algorithm receives an ImageID as a parameter; the ImageID serves as a cryptographic identifier for the expected ELF binary.
Deploying a zkVM Application
Once you've built a zkVM application, you can generate proofs on your own machine(s) or you can make requests to Bonsai to generate proofs as needed.
For local proof generation, we recommend a machine with at least 16GB of RAM. Options for generating proofs using GPU acceleration and skipping proof generation are documented in the feature flags.
Next Steps
Ready to start building zkVM applications?
Check out zkVM Quickstart & Guest Code 101.
Want to browse some demos?
Check out the zkVM example applications.
Curious about performance?
Check the performance benchmarks page.
Looking for information about blockchain integration?
Check out Bonsai.
Curious about Zeth?
Read the article.